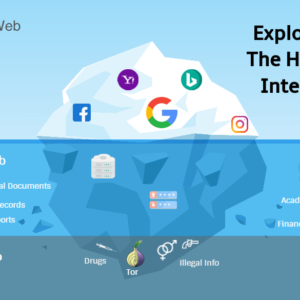
The surface Web is important because the network is evolving over the world. According to some conclusions, there were approximately three hundred million internet prime category domain phrases enrolled worldwide in the second part of the year, 2016. It is an approximate twelve percent improvement from the abundance of domain terms enrolled in the exact duration in the year 2015. As of upcoming years, there were calculated to be further than approximately 1.154 billion online websites. As investigators have reported, regardless, these abundances are just an indication of the extent of the Web, as abundances of stoners and webpages are continually fluctuating. Then the deep web is available. TorDex subjects on that web page are for enlightening motives. The Deep Web, as prominent, cannot be processed by conventional search engines due to the subject in this covering of the web not existing or organized. Data there is not fixed and correlated to different sites as is data in the Surface Web. The experimenters have pointed out, it is virtually unthinkable to calculate the extent of that deep web. While many early conclusions settle the extent of the deep web at approximately 4000 to 5000 times bigger than that, surface web, the shifting dynamics of how data is processed and illustrated by norms, the Deep Web is evolving exponentially and greatly. Within the Deep Web, the Dark Web is further evolving as different equipment give rise to it being easy to navigate. Because someone may process or access that particular Dark Web speculating on a slight threat of detecting something, they would employ this setting for a variety of valid and illicit actions. It is ambiguous, still, how extensively the Deep Web is adopted by that Dark Web subject and then how much of that Dark Web is employed for valid or illicit actions. Tor relates both to that software which someone installs on their computer to operate Tor and those networks of computers that organize Tor website connections. People who use Tor’s connect to web pages through a procession of actual shafts relatively than giving rise to an immediate relation, thus authorizing both institutions and people to stake data over common systems without negotiating their privacy aspects. Users route their network traffic through different stoners’ computers so that the network traffic should not be tracked to the actual user. Tor virtually ascertains coverings such as coatings of an onion and paths traffic or website traffic difficulty through those coverings to suppress stoners’ identities. Want to bring between layer and layer, that Tor has ascertained contests on computers all around the globe through that information passing. Data is encrypted between each relay, and all the Tor traffic ratifies through a minimum of three relays to attain its desired destination. The ultimate relay is named the exit relay, and the Internet Protocol address or other IP address of that relay is perceived as the reference of the specific Tor traffic. When employing Tor software, people’s IP addresses reside concealed. It occurs that the communion to any provided website appears from that particular IP address of that ultimate Tor exit relay that would be anywhere on the planet.